
The Dark Side of Innovation
In today’s hyper-connected world, technology can be a double-edged sword. While it has transformed communication, commerce, and security, the misuse of technology to spread terror has emerged as a growing threat. A recent incident involving Mossad’s use of modified pagers to stage a cyber-physical attack in Lebanon demonstrates the dangerous potential of technological exploitation for malicious purposes.
The Mossad Operation: A Case of Technological Subversion
In a chilling operation, Israeli intelligence agency Mossad reportedly manipulated pagers at the production stage to plant two ounces of explosives and install a remotely operated switch capable of triggering blasts. The pagers, which were manufactured by BAC Consulting KFT in Hungary and sold under the Taiwanese brand Apollo Gold, were used by Hezbollah members in Lebanon.
A message was sent to the pagers, appearing as if it came from Hezbollah’s leadership, causing confusion and alarm. In response, thousands of pagers exploded simultaneously, causing widespread panic. The batteries, capable of burning up to 590°C when ignited, contributed to the intensity of the explosions. Shockingly, the devices were imported through legitimate channels and carried by adults and children alike. Walkie-talkies held by Hezbollah members were similarly compromised.

Image Credits: Deccan Herald
While this attack was a direct hit against Hezbollah, the ripple effect of such an operation raised alarms about the broader misuse of technology in conflict zones. Lebanon, unfortunately, became the testing ground for a large-scale cyber attack aimed at causing havoc and fear.
Lessons for India: Measures to Prevent Technological Misuse in Terrorism
India, as a major player on the global technological stage and a frequent target of terrorism, must remain vigilant against the possibility of similar attacks. Here are several critical measures that can be implemented to avoid such acts of terror:
1. Stricter Import Regulations for Electronic Devices
The attack in Lebanon highlights how off-the-shelf electronics, such as pagers and radios, can be weaponized at the production stage. India must enforce stricter regulations for the import of electronic devices, especially from foreign manufacturers. Mandatory security checks, including hardware verification and integrity tests, should be conducted on all communication devices entering the country.

Image Credits: Business Today
2. Cybersecurity Audits for Electronic Manufacturers
Local and international manufacturers of communication devices should undergo regular cybersecurity audits to ensure that their products are secure from manipulation. These audits should include checks on the entire supply chain, from raw materials to production and distribution.
3. Collaboration Between Cybersecurity Agencies and Intelligence Networks
India’s cybersecurity agencies, such as CERT-In, should work closely with national intelligence services like RAW and the NIA to share information on potential threats. Intelligence gathered through Open Source Intelligence (OSINT) and the dark web, similar to how this case was tracked, can provide valuable leads to thwart such attacks.
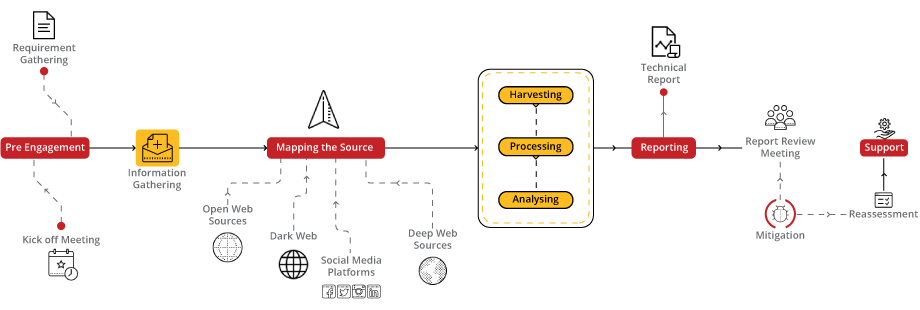
Image Credits: Briskinfosec
4. Strict Surveillance on Foreign Procurement by Suspected Groups
Any suspicious procurement of communication devices by extremist groups, both domestic and foreign, should be thoroughly investigated. Monitoring the purchase of devices like walkie-talkies, pagers, or other communication equipment through advanced AI and machine learning technologies can help detect unusual purchasing patterns.
5. Advanced Forensic Analysis and Reverse Engineering
Post-blast forensic analysis should include not just physical remnants but also a detailed reverse engineering of the electronic components. This would help identify the origin of the hardware and the nature of tampering, providing critical clues about the source and extent of the operation.

6. Public Awareness and Reporting Systems
Public awareness campaigns can help prevent potential terror attacks by educating people about the risks associated with unverified electronics. Additionally, a robust reporting system should be set up, encouraging citizens to report suspicious devices or unexplained malfunctions in communication equipment.
7. International Collaboration on Cyber Terrorism
Since terrorism often transcends borders, India must work closely with international cybersecurity organizations and allied nations to share intelligence and best practices. Collaborative efforts can help identify and prevent cyber-physical attacks before they reach Indian shores.

The Mossad operation in Lebanon serves as a stark reminder of how technology can be twisted to serve malevolent purposes. As technological advancement accelerates, so does the ingenuity of those who seek to cause harm.
By implementing stringent security measures, encouraging public vigilance, and fostering international collaboration, India can better protect itself from the growing threat of technologically facilitated terrorism.
The fight against cyber-terrorism must evolve hand-in-hand with the rapid pace of technological innovation, ensuring that the tools designed to connect us do not become instruments of destruction.
IS360 Can be Reached at
Sharing is caring!

